Fastman Permissions Manager
Understand Access. Take Action. Manage with Confidence.
Manage user permissions, security and compliance from a single dashboard with complete visibility.
Protect your Content Management data with confidence
Spot access issues and irregularities in seconds
Run fast, accurate permissions audits
Managing permissions in an a safe and cost-effective manner is challenging
- Frustrated you can’t safely make permissions changes in bulk.
- Annoyed about relying on IT or a service desk to perform simple permissions tasks.
- Concerned you’re not able to identify the extent of any permissions breach.
- Afraid you don't have the means to effectively resolve permission anomalies if they occur.
An essential component of your information control implementation
Managing security and access within your Extended ECM platform is crucial. Permissions Manager is an essential component for your implementation, providing critical capabilities that enable administrators and power-users to quickly identify, address, and avoid information leaks. It serves as the brains behind all sound internal information control solutions.
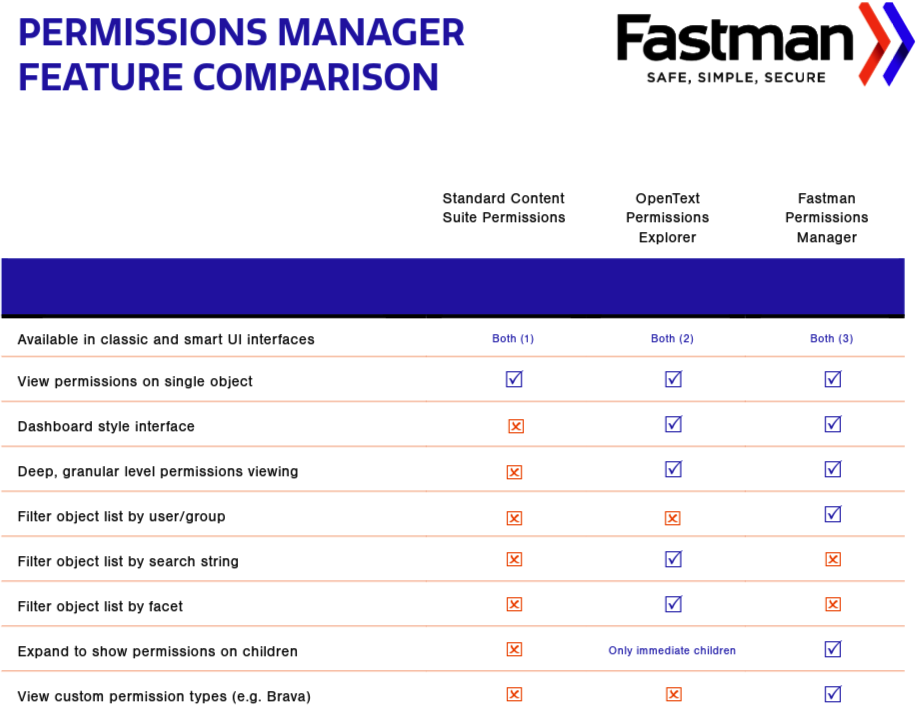
A detailed overview to quickly spot discrepancies
Permissions Manager makes the complex simple. The ability to view information on individual folders, across collections of content, or throughout the whole repository makes complex information security structures manageable.
Permissions Manager also provides permissions roll-back, search, and detailed audit logs that deliver a level of control far beyond those available in the standard Extended ECM.
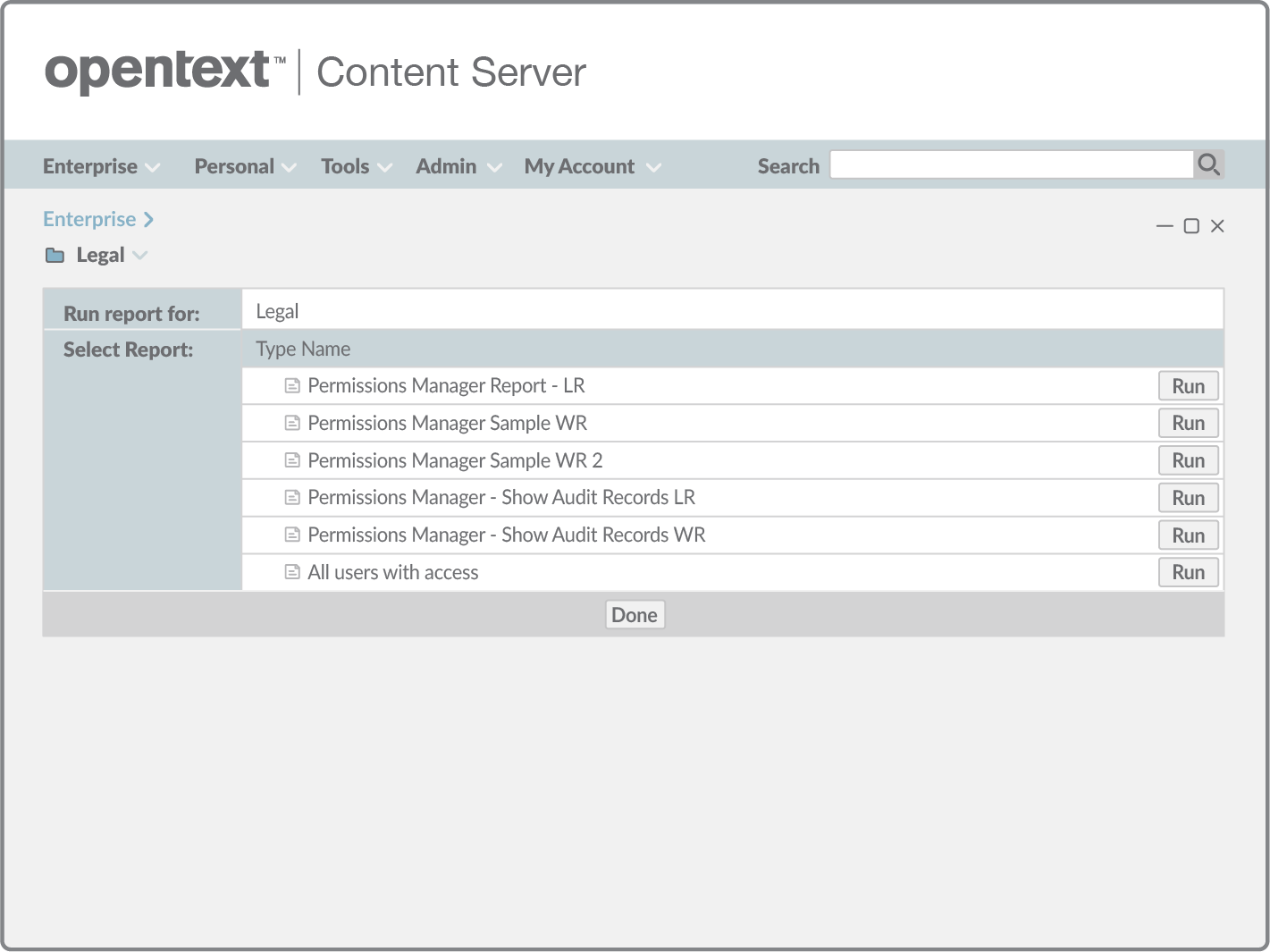
Off-the-shelf and operational within hours
Implementing Fastman Permissions Manager requires no professional services or supplementary development effort. It is fully supported, installs out-of-the-box, can be operational in hours and is proven with organizations around the world.
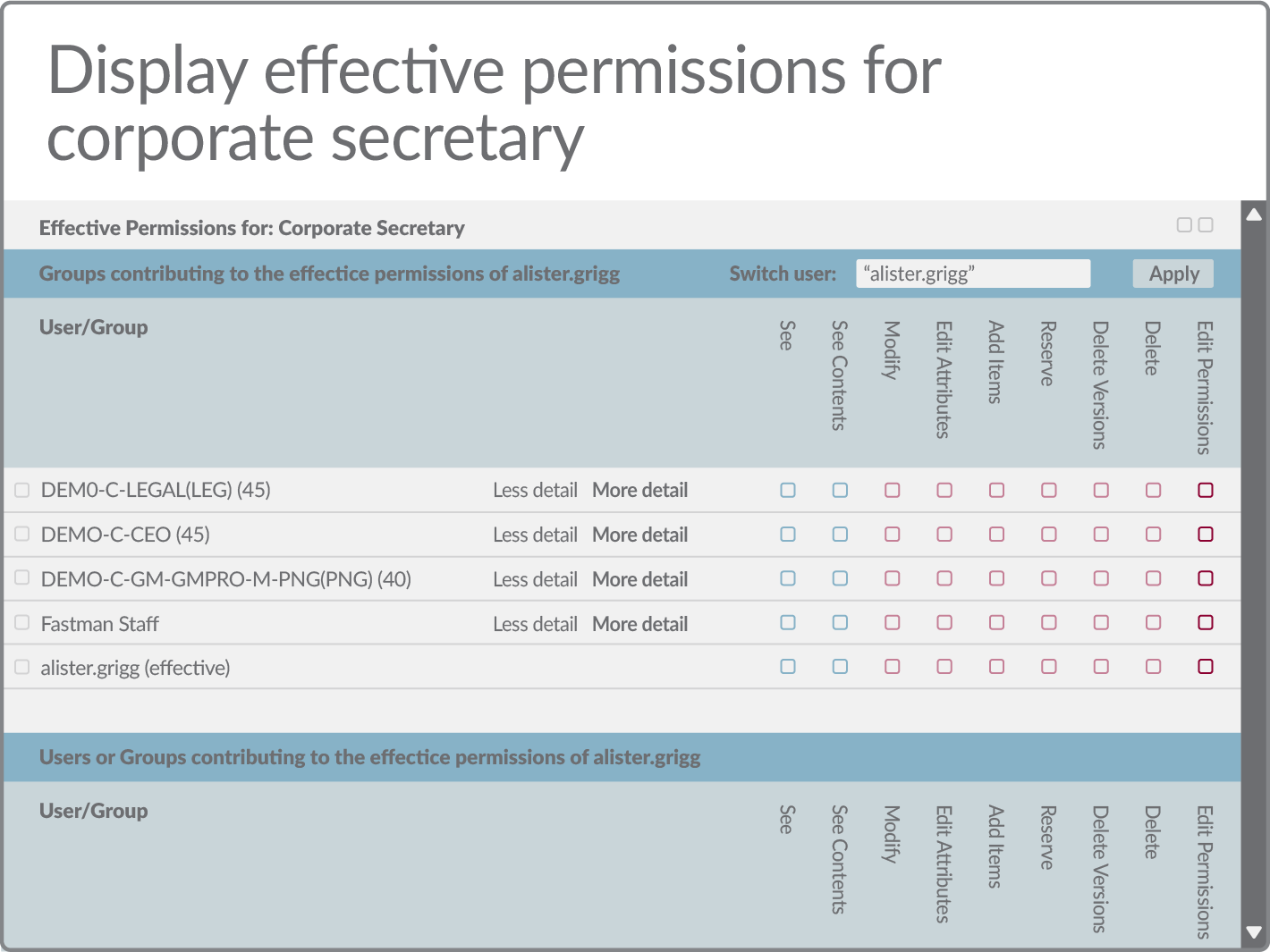
Reduce the burden of permissions administration
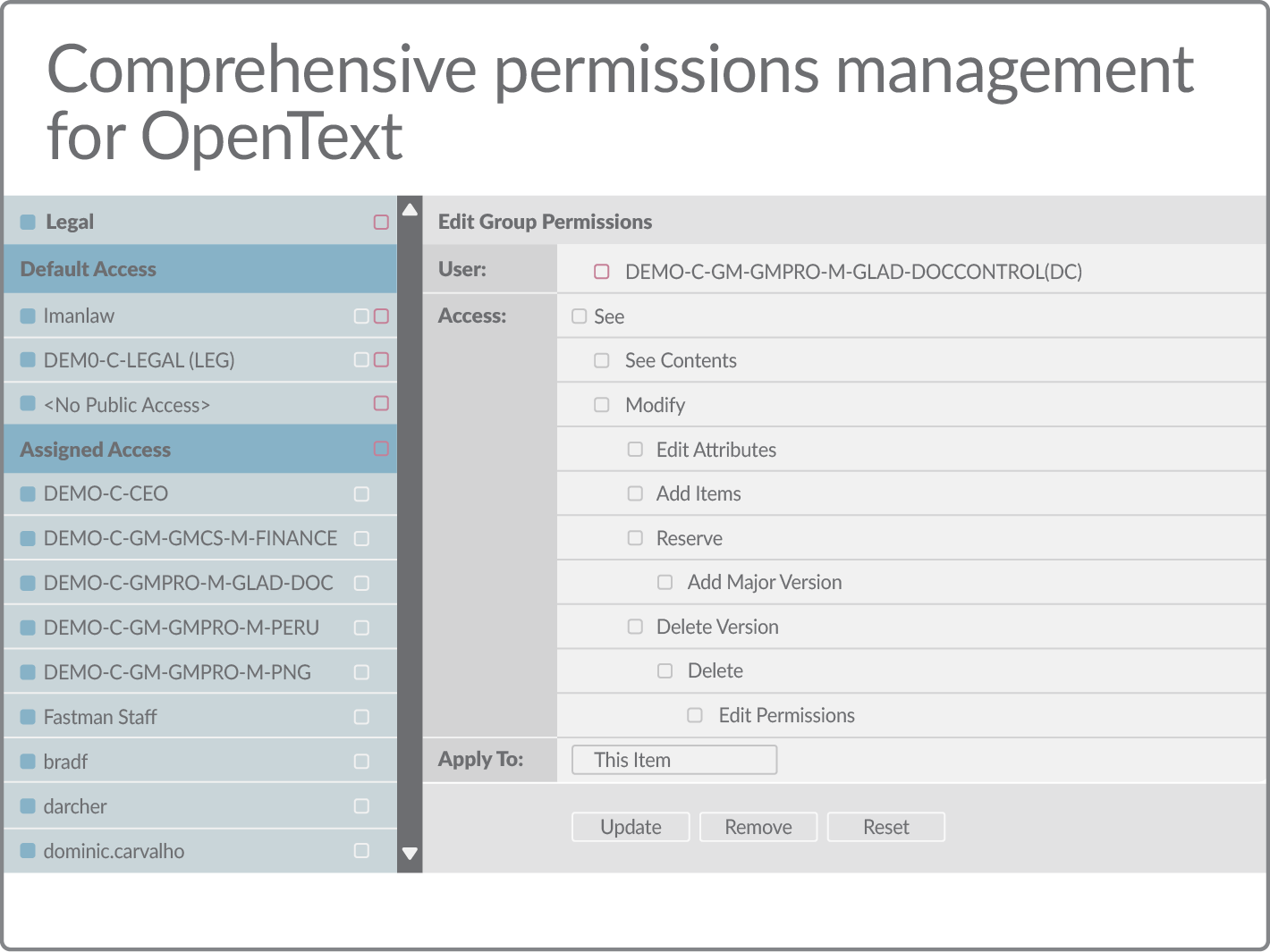
Through its decentralized approach, Permissions Manager enables business users to retain control of their own data.
The simple and easy to use tools it provides enable individual users to view and take action on permissions, including applying approved access templates. Business teams no longer need to turn to IT or the service desk to perform basic tasks.
Permissions Manager also provides a comprehensive set of usage controls. From specific functions, down to individual users, it allows administrators to define exactly what can be done and by whom.
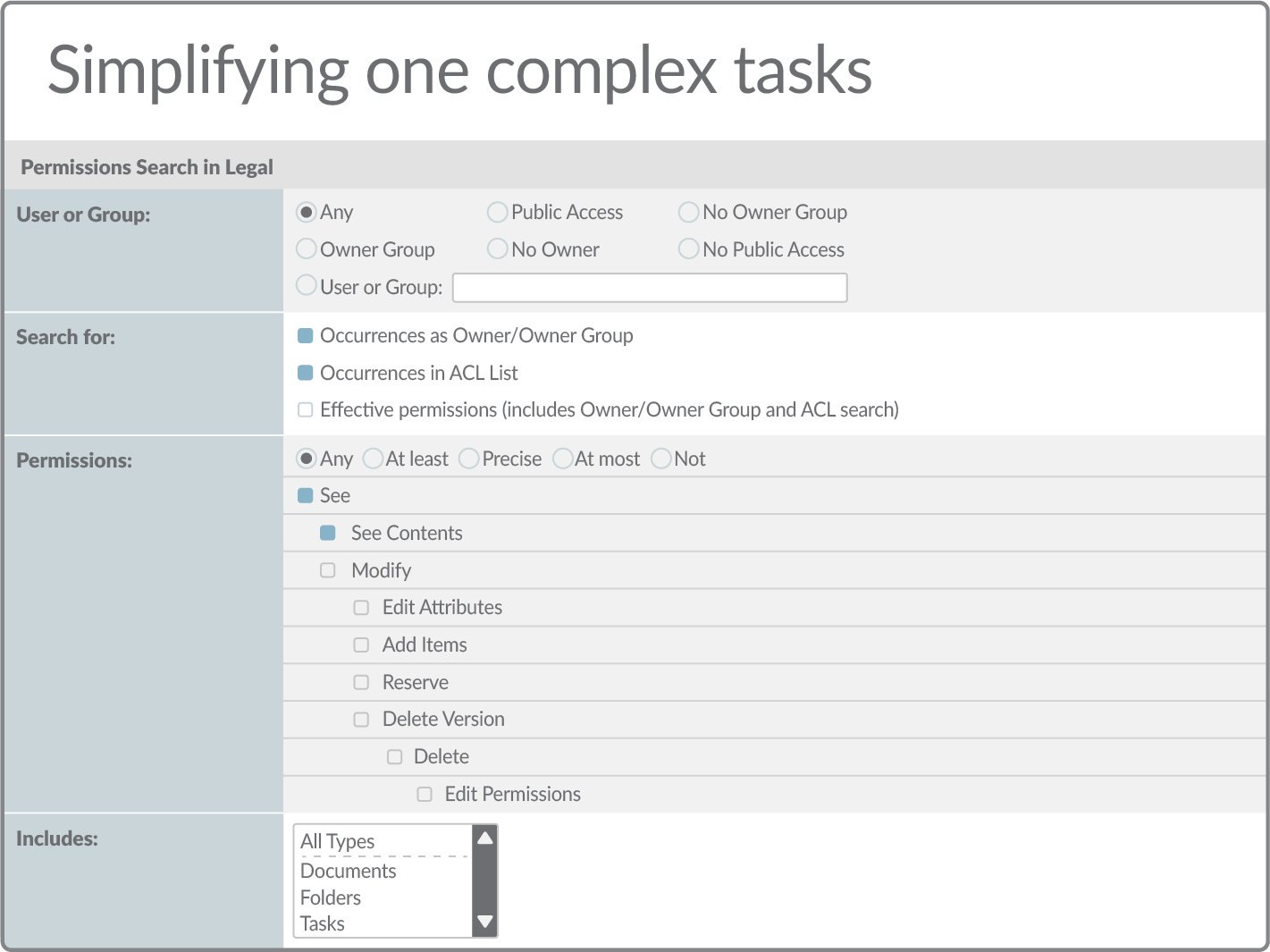
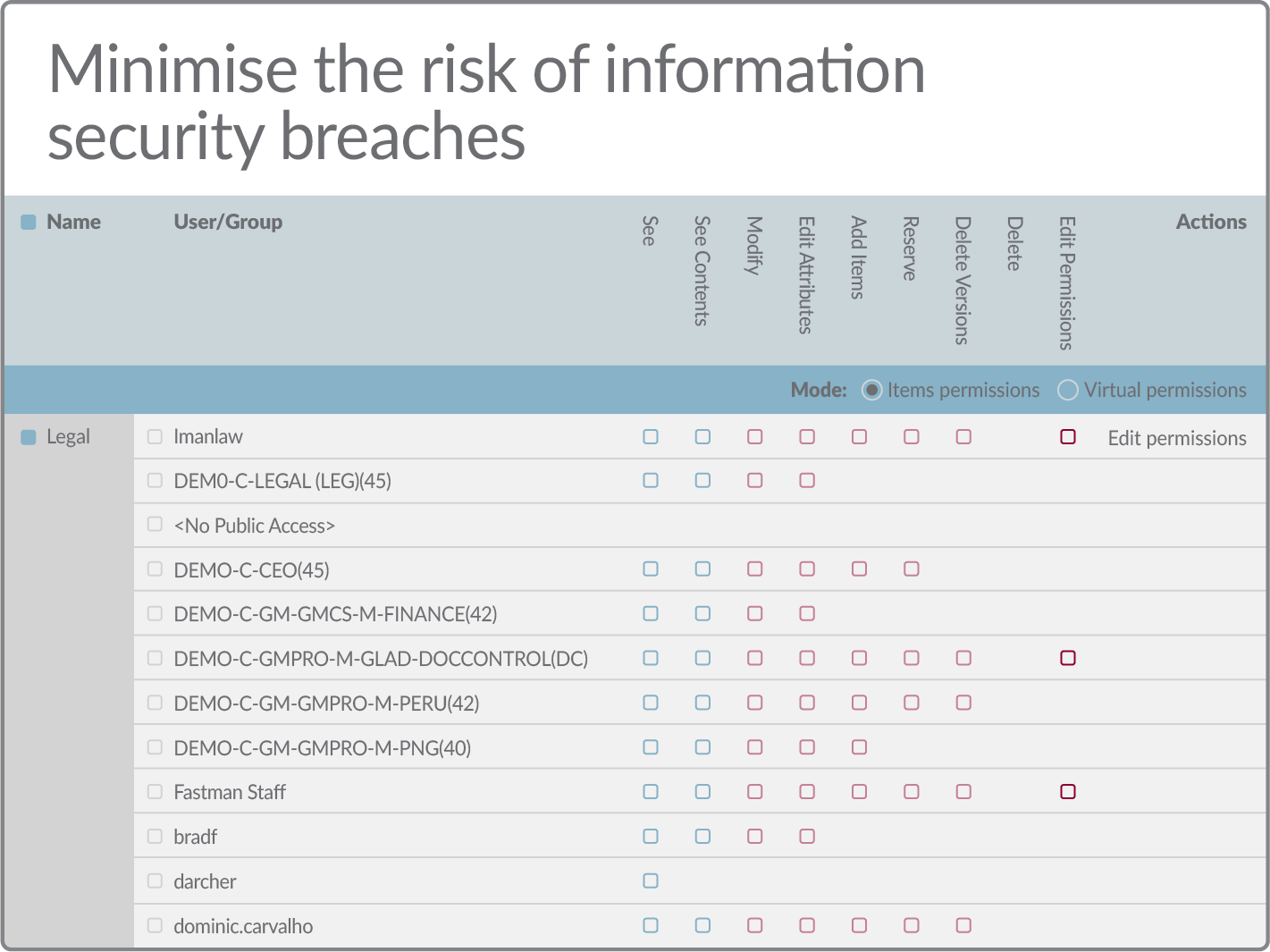
Manage complex information security structures
Permissions Manager makes the complex simple. The ability to view information on individual folders, across collections of content, or throughout the whole repository makes complex information security structures manageable.
Permissions Manager also provides permissions roll-back, search, and detailed audit logs that deliver a level of control far beyond those available in the standard Extended ECM.
Related Assets
It's time to trust your information…

1. Arrange a meeting
We will review your information handling processes and provide steps to ensure integrity.

2. Take action
Design and implement your digital signing environment, ensuring that it is tightly integrated with your business processes.
.png)
3. Trust your content
With technology and processes in place, you can trust the integrity of your platform and the information within.